There’s a scam making the rounds on Facebook, making use of Facebook Messenger to spread. (Sysadmins, scroll to the bottom for a list of domains to block).
It starts when you receive a message from a friend, that simply says your name, with your profile picture designed to look like a preview of a video with hundreds of thousands of views. The implication is there is a “Facebook Video” of you that has gone viral.
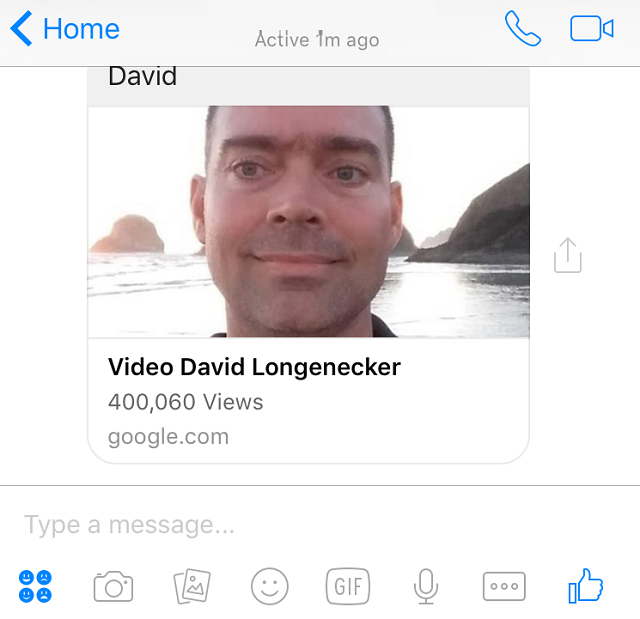
Of course, this implication is false. When you click the image to see the video, one of a few things happens. On a PC, the link goes through a few forwarding addresses and ends up at a blank BlogSpot website. On mobile devices, you may see a message indicating you have won something, or you may see what appears to be a login screen for “Facebook Videos.” I’ve attached some screen shots below.
The “Facebook Videos” login screen is a phishing scam: if you “log in,” you are in fact giving your password to the scammer, who will immediately turn around and send the “video” bait to all of your contacts. This is how the scam spreads to new potential victims. I am fairly certain this is automated, effectively making this a Facebook worm that spreads as rapidly as people can be tricked.
As for the so-called prizes: more than likely, victims that try to claim the prizes will be asked for personal information and some sort of payment for “shipping fees.” Of course, there are no prizes, and anything that victims pay will be gone.
What can you do?
- Be very, very skeptical of any link that asks you to log in – especially if it asks you to log into the same service you got the link from (for example, a link in Facebook asking you to log into Facebook). There are very few occasions where this would legitimately occur.
- Enable “Login Verification” for your Facebook account. In the Settings menu, go into Security Settings, and check the box beside Login Verification. With this enabled, logging into Facebook from any new device requires both your password, and either a code sent to you by text message, or a code delivered through the Facebook mobile app on a device you already trust. Simply put, a stolen password is useless to a crook unless they also have control of your phone.
- If you do fall for this scam, don’t beat yourself up. The scam is designed to be believable. Change your password immediately – and then use the Security Settings menu to see where your account is logged in. You can kill off any other logged in sessions (including the device the crook has logged into).
Desktop versus Mobile differences
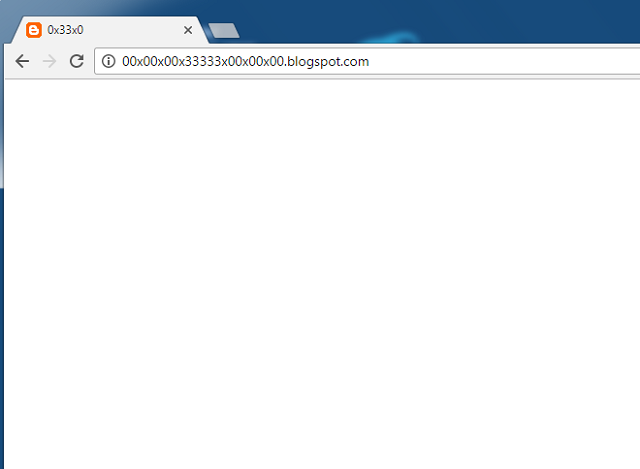
Interestingly, this scam detects what sort of device you are using, and adjusts the destination accordingly. After hopping through a Google URL forwarder and Google Translate (presumably to thwart security systems that detect malicious links embedded in email), I anded up at http://00x00x00x33333x00x00x00(.)blogspot(.)com, which contained the following Javascript:
var device = navigator.userAgent
if (device.match(/Iphone/i)|| device.match(/Ipod/i)|| device.match(/Android/i)|| device.match(/J2ME/i)|| device.match(/BlackBerry/i)|| device.match(/iPhone|iPad|iPod/i)|| device.match(/Opera Mini/i)|| device.match(/IEMobile/i)|| device.match(/Mobile/i)|| device.match(/Windows Phone/i)|| device.match(/windows mobile/i)|| device.match(/windows ce/i)|| device.match(/webOS/i)|| device.match(/palm/i)|| device.match(/bada/i)|| device.match(/series60/i)|| device.match(/nokia/i)|| device.match(/symbian/i)|| device.match(/HTC/i))
{
window.location = "http://00x00x00x00xchocholox000.blogspot.com/?"+ h(7, '')+"";
}else
{
}
This snippet of code checks for about 20 flavors of mobile browser of mobile operating system, and if it finds a match, it instructs the browser to go to http://00x00x00x00xchocholox000(.)blogspot(.)com; otherwise it continues to load the current page.
At the time that I analyzed the code, the former page either had an error or had been disabled; on a PC it displayed only the following:
Example "prizes" and the "Facebook Videos" phish


Sample malicious links
The "video" link in Messenger uses google(.)com/url to redirect to translate(.)google(.)com, which in turn loads the actual malicious landing page. The landing page either randomly or through logic I have not yet identified, redirects to destinations including the following:
00x00x00x00xchocholox000(.)blogspot(.)com
00x00x00x33333x00x00x00(.)blogspot(.)com
00x00x00x33333x00x00x00(.)blogspot(.)com
sddzz(.)offer(.)negix(.)xyz
facebook(.)com-prize-win6(.)us
login-video(.)l0ginxvide0s(.)com
login-video(.)appxvide0s(.)com
seekverify(.)com
https://pf(.)media-rocks(.)com/
login-video(.)appxvide0s(.)com
seekverify(.)com
https://pf(.)media-rocks(.)com/