
Every now and then, my day job pays dividends at home. Shortly before Christmas was one such occasion.
My daughter (a foreign exchange student my family is hosting, but she quickly became a daughter to us) had just spent a weekend with a friend. The friend too was a foreign exchange student from the same country as my daughter, but was near the end of her exchange, and was soon to return to her their home country. My daughter had taken many pictures of their weekend together, and had uploaded them to the friend's computer.
As is commonly the default, uploading the photos to the computer also deleted them from her camera.
By the time she discovered that, the friend had already begun her trek home. Several gigabytes of photos are not hard to transfer over WiFi or with a flash drive ... it's a different story when all you have is a cellphone hotspot with a limited data plan, or a costly and rate-limited airport wireless service.
Much to my wife's chagrin I am a sucker for my daughters' pleas for help. That holds true whether from the daughters born to my family or the daughter we are hosting. Just about any dad would say the same. Fortunately, one doesn't spend twenty years in technology and digital forensics without learning a few tricks.
Computers (or their developers) are lazy. Modern filesystems work by storing data on the digital storage media, then keeping a record of what data is where. The technical term for this is the "master file table" or MFT, but you could think of it as a table of contents. If I open File Explorer to see what is on the disk, I'm not seeing the actual files - I am just looking at that table of contents. When I delete a file, the computer doesn't erase the contents of that file - it just removes the file from the table of contents.
Eventually the computer will reuse the space that the file occupied - but until that happens, the contents of that file still exist on the disk. Computer forensics (and an element of espionage) relies on that fact. With the right software, it is possible to find files thought to have been deleted from a computer.
Like many cameras, my daughter's uses a removable SD card, so the first step was to insert the disk into my PC. My laptop has a slot for SD cards, but if yours does not, they are readily and cheaply available on Amazon and elsewhere.
A visit to any search engine will offer many possible data recovery programs - some safe, and many not so safe. Thankfully I have used a few file recovery programs that I know to be safe. In this case, I used PhotoRec, written by French developer Christophe Grenier, and available for free from www.cgsecurity.org/wiki/PhotoRec.
From a windows command prompt, the next step is to run photorec.exe. It starts with a list of physical storage devices (hard drives, CD or Blu-Ray drives, flash drives, etc.) it finds on the computer:
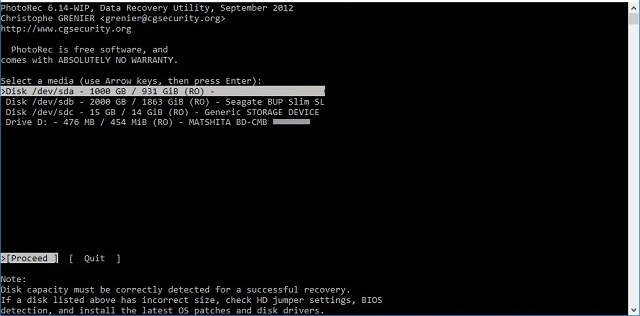
In this case, I have four storage devices available:
/dev/sda is a 1 terabyte (1000GB) hard disk in my laptop
/dev/sdb is a 2 terabyte external hard disk connected to a USB port
/dev/sdc is a 15GB "generic storage device"
Drive D is a Matshita blu-ray and CD combo drive plugged in to a USB port
/dev/sdc - the "generic storage device" - is the SD card I am interested in, so I used the arrow keys to select that line, and pressed "Enter."
A storage disk is just a bunch of magnetic bits; they can be positively or negatively charged, representing zeros and ones. Computer filesystems define "partitions," or logical pieces of storage. This is how you might have a C: drive and a D: drive on a laptop, even though it has only one physical hard drive.
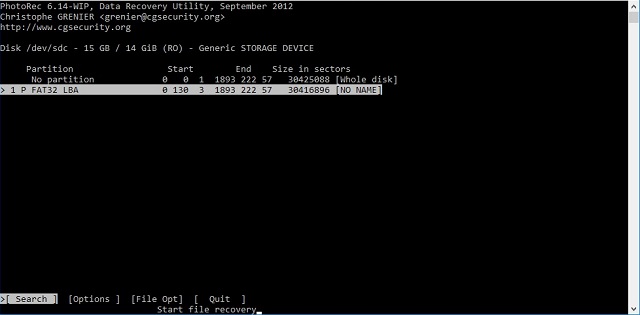
I chose the defined partition "NO NAME" since any files would have been saved on the defined partition.
Next, PhotoRec needed to know what format the filesystem is. Different computers (Windows, Linux, Mac OS) use different formats.
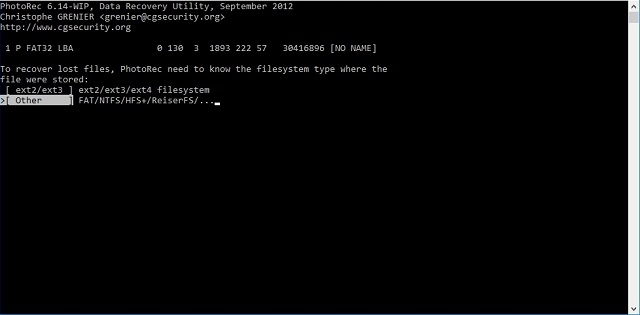
A very common format is FAT (short for "File Allocation Table"). I thought that the most likely format that a camera would use, so I selected the format option that included FAT.
Next, PhotoRec wants to know if I want to look at the entire partition, or only at the unallocated space.
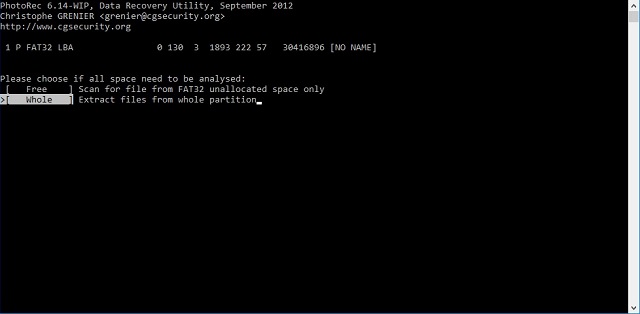
Truth be told, searching unallocated space (in other words, space that the "table of contents" believes to be free space - which includes files deleted from the table of contents) would probably have been faster, but I chose to search the entire partition just to be thorough.

And now we wait. The "estimated time to completion" of 46 hours is actually on the long side - the tool took only a couple of hours to retrieve every deleted file that had not been overwritten - including the precious photos my daughter had lost.
Mission accomplished: through the magic of digital forensics, I have convinced my daughter that I am both a wizard and her hero!
