For Windows XP users, the grace period lasted about 3 weeks longer than expected, but it's over now. The first of what will likely be many never-to-be-fixed bugs has turned up, and it's a doozy.
Security firm FireEye this weekend reported a serious flaw in versions of Internet Explorer from IE6 through the latest and greatest IE11. Thus far active exploit in the wild has focused on IE 9 though 11 (which will not run on Windows XP), but this will surely change now that it is public. For a mind-bendingly thorough discussion of how the vulnerability is exploited, see FireEye's write-up. The Cliff Notes version is this: the attacker makes use of an Adobe Flash Player technique that bypasses some IE security measures, drops its own code into a certain point in memory, and then through the newly-discovered bug executes that code.
The even simpler version is this: if you use Internet Explorer and open up an affected web page (whether a bad site, or a legitimate site that has been compromised, or a malicious email message), the attacker now owns your PC. The truly nasty thing about this sort of bug is that you don't have to do anything unseemly to be hit. Similar vulnerabilities in the past have been exploited through clever advertisements submitted to popular and legitimate web sites.
Tuesday, April 29, 2014
Thursday, April 24, 2014
Password Lessons from Heartbleed
It's been a little over two weeks since the web security bug known as "Heartbleed" was publicly reported (see my earlier post for a description of the bug). For businesses it has meant a lot of scrambling to update servers and to update network intrusion sensors to detect attempts to exploit the bug. Thus far though there have not been widespread reports of data breaches affecting consumers. There was the case of a teenager who was arrested for nabbing 900 social insurance numbers from the Canada Tax Agency (the equivalent of social security numbers and the US IRS) ... note to self: hacking a government agency and then presenting said agency with proof of your hack is not the best way to go about reporting a vulnerability. But I digress...
Monday, April 14, 2014
(CVE-2014-2719) More fun with wireless routers: ASUS wireless routers reveal admin password
If you use an ASUS RT-XXXX wireless router, you should update to firmware 3.0.0.4.374.5517 3.0.0.374.5656, released April 24, 2014 (or any newer firmware).
In mid February, I wrote that a substantial portion of ASUS wireless routers would fail to update their firmware. In fact, the "check for update" function would inform the administrator that the router was fully up-to-date, even though it was not. The server tables that identify the correct latest firmware revision for each model of router had not been updated in about 4 months, though there had been two releases in the interim. This was a significant problem because it came right on the heels of an exploit for a bug in which hard drives connected to the router could be accessed from the public Internet, with no login credentials required.
In mid February, I wrote that a substantial portion of ASUS wireless routers would fail to update their firmware. In fact, the "check for update" function would inform the administrator that the router was fully up-to-date, even though it was not. The server tables that identify the correct latest firmware revision for each model of router had not been updated in about 4 months, though there had been two releases in the interim. This was a significant problem because it came right on the heels of an exploit for a bug in which hard drives connected to the router could be accessed from the public Internet, with no login credentials required.
Wednesday, April 9, 2014
OpenSSL Heartbleed: What does broken encryption actually mean?
The Internet is full of hyperbole, exaggerations, "the sky is falling tales" and the like. To be fair, there are lots of ways bad actors can cause trouble, but in most cases reality falls a bit short of the hype.
That may not be true in this case. Researchers Monday night published a report on the so-called "Heartbleed" bug, named for the heartbeat function it affects in the popular OpenSSL library. OpenSSL is used by many, many websites to enable encrypted communication between you and the web site. When you see the "padlock" icon in your browser window, it means your communication is encrypted - more often than not, that is OpenSSL at work.
That may not be true in this case. Researchers Monday night published a report on the so-called "Heartbleed" bug, named for the heartbeat function it affects in the popular OpenSSL library. OpenSSL is used by many, many websites to enable encrypted communication between you and the web site. When you see the "padlock" icon in your browser window, it means your communication is encrypted - more often than not, that is OpenSSL at work.
Tuesday, April 8, 2014
10 things to do with an old Windows XP PC
Today Microsoft will release the final updates for Windows XP, the once-novel, oft-maligned, and persistently enduring operating system. Microsoft has provided stability and security updates for 12 years but will no longer do so after today.
What does this mean to you? If you have a PC bought in about the past 5 years or so, nothing. Most if not all PCs bought since late 2009 came with Windows 7, which according to the current roadmap will be supported through 2020. (If you bought between early 2007 and late 2009, and did not manage to upgrade, you may have been stuck with the quite unpopular Windows Vista, but still have a few years of Microsoft support left).
But for the millions still running Windows XP at home (and even more importantly, for the operators of millions of ATMs and point-of-sale registers running embedded Windows XP) there are some very real implications. 12 years of updates have resulted in a pretty stable operating system, and the most egregious security flaws have been fixed (at least the known ones). In its early years, Windows XP was riddled with holes that lead to such malware fiascoes as Code Red and Nimda, Internet worms that crashed millions of PCs and brought businesses to their knees for days or even weeks. That has not been the case lately.
What does this mean to you? If you have a PC bought in about the past 5 years or so, nothing. Most if not all PCs bought since late 2009 came with Windows 7, which according to the current roadmap will be supported through 2020. (If you bought between early 2007 and late 2009, and did not manage to upgrade, you may have been stuck with the quite unpopular Windows Vista, but still have a few years of Microsoft support left).
But for the millions still running Windows XP at home (and even more importantly, for the operators of millions of ATMs and point-of-sale registers running embedded Windows XP) there are some very real implications. 12 years of updates have resulted in a pretty stable operating system, and the most egregious security flaws have been fixed (at least the known ones). In its early years, Windows XP was riddled with holes that lead to such malware fiascoes as Code Red and Nimda, Internet worms that crashed millions of PCs and brought businesses to their knees for days or even weeks. That has not been the case lately.
Friday, April 4, 2014
Credit Cards for 1.2 Million Drivers Vulnerable at TxTag.org
It's been a bad couple of weeks for transportation authorities in the two biggest US states. On March 22, Brian Krebs broke the story of a wide-ranging credit card breach at the California DMV. That breach apparently involved credit cards used at the CA DMV's online web site over a 6 month period from August 2013 to January 2014.
Today I discovered a serious flaw at TxTag.org, the Texas Department of Transportation's toll road account management and payment system. This flaw exposes personal information for the (as of December 31) 1.2 million drivers with active TxTags, including names, full mailing addresses, email addresses, phone numbers, and credit card numbers with expiration date.
Today I discovered a serious flaw at TxTag.org, the Texas Department of Transportation's toll road account management and payment system. This flaw exposes personal information for the (as of December 31) 1.2 million drivers with active TxTags, including names, full mailing addresses, email addresses, phone numbers, and credit card numbers with expiration date.
Wednesday, April 2, 2014
Misguided by Google Maps
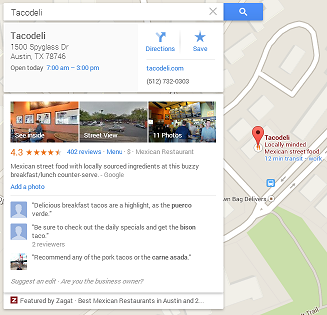
In late February, a security consultant described a way of gaming Google Map's crowd-sourced "places" system to create fake places, or to give false locations and phone numbers for real places. The researcher showed either real chutzpah, or a serious lack of common sense, in his choice of example: he created Google Maps places for a US Secret Service office and an FBI office. Instead of publishing the legitimate phone numbers for these offices though, he published his own phone number, which he set up to forward the call to the legitimate office while recording the conversation. Within 24 hours he received and recorded 15 calls, including one from a local police officer wanting to discuss a counterfeit money bust.
Tuesday, April 1, 2014
Raspberry Pi: The $35 Computer That Does Everything [April Fools Edition]
The below is an April
Fool's Day post. While the Raspberry Pi is a capable little device, at an
outstanding price for a learner box, it cannot actually access the future. Nor
is there actually such a thing as amadán aibreán (i.e. "April Fool") radiation.
Watch here for a write up of some real-world applications in coming
weeks!
The Raspberry Pi debuted about 2 years ago, the culmination of a 6-year dream to make a PC tiny enough and cheap enough to restore some of the "hobby hacking" culture of a generation ago. My generation grew up tinkering with DOS-based PCs, Apple II Macs, Commodore 64s, Amigas, and the like - computers that required a bit of hands-on programming and tuning to get the most out of them. Much (not all) of that tinkering culture faded with the advent of graphical interfaces, and later, touch screens, that abstract the nuts and bolts from the end user experience. The evolution of user experience has brought about amazing things, there's less opportunity to "MacGyver" a touch screen.
The Raspberry Pi debuted about 2 years ago, the culmination of a 6-year dream to make a PC tiny enough and cheap enough to restore some of the "hobby hacking" culture of a generation ago. My generation grew up tinkering with DOS-based PCs, Apple II Macs, Commodore 64s, Amigas, and the like - computers that required a bit of hands-on programming and tuning to get the most out of them. Much (not all) of that tinkering culture faded with the advent of graphical interfaces, and later, touch screens, that abstract the nuts and bolts from the end user experience. The evolution of user experience has brought about amazing things, there's less opportunity to "MacGyver" a touch screen.