
Friends and family regularly send me things they find suspicious or weird. Sometimes it turns out to be malicious, and other times perfectly fine, but I'm always glad to know I've instilled a proper degree of skepticism in my friends.
My willingness to help has an ulterior motive: aside from the "herd immunity" that comes from helping those around me stay safe, analyzing weird things they see helps me keep my own skills sharp. It also can alert me to new or resurging threats, such as the Disney theme park scams so common around customary family travel periods.
Today's story is about a phish. A simple phish, but one with lots of red flags to call out, and that called to my attention some new features Google introduced in Chrome last month. As with many phish, this one begins with an email. Nothing fancy, just a brief memo that a voice message has arrived.
Red Flag #1: an obviously spoofed sender.

The email says it comes from Microsoft Corporation, but the address beside the label is actually [email protected]. The domain q.com belongs to Qwest Communications, a holding company for Internet Service Providers including Qwest and CenturyLink. Most likely, this is the home email of someone whose email password was stolen, and whose email account is now being used to send phishing spam. I've anonymized the actual user since they are no doubt just a pawn in this game.
The sender makes a minimal effort to look legitimate, by spoofing the sender's email address to read "Microsoft Corporation." Depending on the mail client, the sender may appear as "Microsoft Corporation" or "Microsoft Corporation <[email protected]>", or as in this screen capture, "Microsoft Corporation [mailto:[email protected]]"
Much like the return address on a physical letter is no guarantee of where that letter was mailed, the "from" label on an email is no guarantee of its origin. In most email clients however, you can hover your mouse over the displayed name and see the actual return address. That too can be manipulated, but it's a bit more reliable than the displayed name.
Red Flag #2: an out-of-context attachment.

At this point, there are a few things I do to analyze the attachment before I go any further. The first is to run Didier Stevens' PDF Tools to see what the file contains. Didier is a Belgian researcher who has written a variety of very handy forensic tools that he makes freely available to fellow researchers - his blog is a gold mine for learning file forensics.
Pdfid is a quick-and-dirty count of a few keywords that can tell us useful tidbits about the file. Some common elements in malicious documents are /JS or /JavaScript to indicate the file contains Javascript commands to execute; /EmbeddedFile or /RichMedia to indicate an embedded executable or Flash program; and /AA or /OpenAction to indicate an automatic action to take on opening the document.
If pdfid showed any of these suspicious elements, I would use Didier's pdf-parser (or another favorite, PDFStreamDumper) to take a closer look at the objects contained in the PDF. In this case though, the file contains none of these suspicious elements:

The second thing I commonly do with suspicious files is check them out with VirusTotal.
A caveat: VirusTotal is a malware researcher's best friend - uploaded files will be analyzed by about 50 malware detection products, and cumulative results displayed on the screen. However, any file uploaded for analysis also becomes available for other researchers (as well as malware authors) to download. For routine malware, this is not that big a deal, but if I have reason to suspect something is targeted specifically at me or my organization, I do not want to upload files to VT. Why? Because this lets the attacker know I am on to them. In these cases an alternative is to generate a hash of the file (VT accepts md5, sha1, and sha256) and use the VirusTotal search feature to search for that hash, without uploading the file. In this way I can see if the file has been uploaded by anyone else.
In this case, I was comfortably certain the attachment was a routine phish, so I uploaded it to VirusTotal. It turned out I was the first to upload it, and no antivirus products detected it as malicious. In VirusTotal parlance, the file had a score of "0/54" - out of 54 malware scan engines that tested the file, zero marked it as malicious.
It is not unusual for VT to find no evidence of malice in brand new files: antivirus software is notoriously bad at detecting malicious files it has not seen before. It is much better at protecting you from viruses and trojans that have been around for a few days.
Red Flag #3: an unexpected link in an unsolicited email
At this point I've finished the static portion of my analysis. I have not seen anything to indicate the file is actively malicious, meaning I don't expect anything to blow up simply by opening the file. Still, I won't open it on my everyday system - I move it into a "virtual machine," a virtual computer isolated in a sandbox where it cannot mess with my real computer or network. And I open it:

The PDF is nothing more than an Office365 logo and an instruction to click on a link to listen to the "voice mail" I supposedly have been sent. This is why I found nothing malicious in the static analysis - there was nothing actively malicious to see. This is also why VirusTotal found no evidence of malice: VT is geared more toward viruses and malware, while this phish preys on the human element, asking me to take action myself.
The word HERE is a link to http://peirettisa . com . ar/index.php. My next stop is Bluecoat Webpulse Site Review. Bluecoat makes security appliances including a web proxy, intended to block web requests to known malicious websites. It's a commercial, enterprise grade counterpart to the OpenDNS solution I frequently recommend for home and small business. The Webpulse site review is a quick way to check whether Bluecoat deems a website malicious. In this case, Bluecoat deems this to be a phishing website.

No surprise here.
What is a surprise though is what happens when I follow the link in a handful of browsers.
Red Flag #4: unexpected popup messages, and unexpected "logged out" notices
Opening the link in Chrome for iOS displays a popup message saying "you have been signout [sic] of your Microsoft Account, login to listen to voicemail". This plays into the phish, by explaining the login prompt that comes next.

Red Flag #5: a Google cached copy of a web page
This phish was unusual in that (on Chrome in iOS) the phishing page shown after clicking OK on the popup, is a copy of Google's cached copy of Microsoft Online, complete with the disclaimer Google displays at the top of a cached page. I had a chat with Internet Storm Center handler Xavier Mertens, and neither of us could think of a reason for intentionally imitating a cache versus imitating the real thing. More than likely, the phisher simply got lazy and copied the Microsoft Online webpage out of a Google cache instead of from the live website..

Red Flag #6: Google Safe Browsing warning
Chrome on iOS allowed me to browse directly to the malicious website. Chrome on desktop, however, makes use of Google's Safe Browsing Project, displaying a bright red "danger" screen before allowing me to see the malicious webpage:
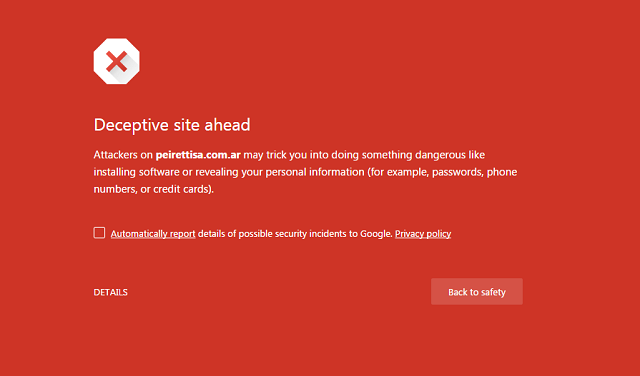
Red Flag #7: Chrome shows a warning right in the address bar

Beginning with Chrome 56 (released in January, 2017), Chrome goes beyond displaying a "lock" icon to represent a secure website. Now, Chrome displays different informational security symbols in the address bar to indicate a secure website, a dangerous or unsecure website, or a website that might or might not represent a risk depending on what you are doing.

Putting the pieces together, here are the phishing page and the real Microsoft Online page, side-by-side so you can see the similarities and differences. Click on the image to open up a high-resolution screen capture.
What can you do to stay safe?
This is a pretty straightforward phishing scam: the attacker compromises an unsuspecting person's email account (probably by stealing a password from a data breach, then turning around and testing to see if the person uses the same password elsewhere). Using the compromised email, the scammer sends lots of phishing messages to targeted victims, in the hopes that some will follow the link, and log into the fake website using their real username and password. Whatever information you enter in the fake website is sent directly to the scammer.
- Use unique passwords for every website that you care about, and use a password manager to remember those many passwords. This ensures that if one password is discovered, it does not unlock every other account you use.
- Enable two-factor or multifactor authentication where you can. 2FA or MFA means logging into your account from a new location or new device requires a code sent to you through SMS, a mobile authenticator app, or some other method. This ensures that a stolen password by itself is not enough for an attacker to take over your accounts - they would also have to steal your mobile phone, or take control of your phone number.
- Set up your home network and your devices to use a DNS or name server such as OpenDNS, that prevents your browser from looking up the address for known-malicious websites. Keep in mind this is not a guaranteed protection - OpenDNS still does not recognize this domain as malicious - but it is generally very effective at stopping common phishing attacks.
- Pay attention to the warnings web browsers are beginning to add.
Forensic notes:
- File name: voice note.pdf
- File MD5: 4a20a0d6fd3f1b9a59bf46f458b5a327
- File SHA1: 0b124d15e3c41fad7c311236746adf1666042cc5
- Phishing domain: http://peirettisa . com . ar/
